How To Use ABS Function In MS Excel
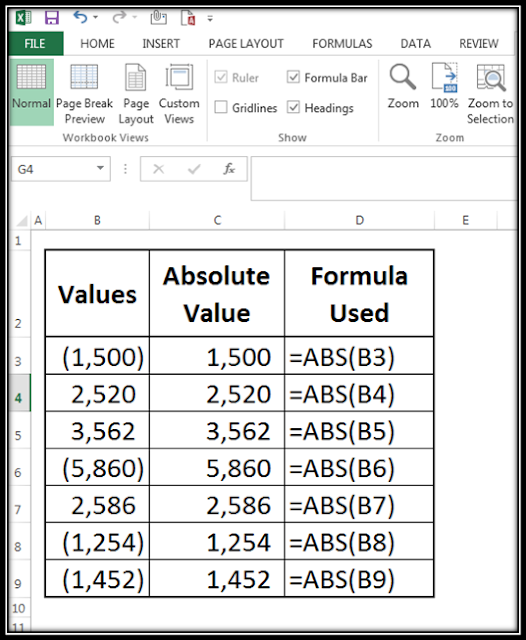
Use of ABS Functions in Microsoft Excel ABS Formula Syntax and usage in MS Excel explanation by ComputerFlicks… The easiest function of Excel, easy to use, and understand. If we need to get the absolute value irrespective of negative or positive, we can use ABS function . As a reference, we can use a number or a cell reference. Let suppose we have huge data that contains positive and negative values, but our requirement is to get the sum of all values. For example, we have two values +20 and -20 , if we add both values it will be zero, instead of zero we want the sum of both values "40" . In such cases the first step is to use ABS function and convert all values into absolute values, after getting absolute values, we can add both values and we will get the output "40" . Syntax: = ABS (number) We place the number of which we want the absolute value. In the place of no we can also select the cell reference in the excel sheet. Imag...

